ABOUT CENTRIC
CENTRIC proposes to leverage Artificial Intelligence (AI) techniques through a top-down, modular approach to wireless connectivity that puts the users’ communication needs and environmental constraints at the center of the network stack design. It all starts with the users’ objectives and application-specific requirements. Then, AI techniques are used to create and customize tailor-made waveforms, transceivers, signaling, protocols and RRM procedures to support these requirements. This is the user-centric AI Air Interface (AI-AI) that CENTRIC will enable.
To guarantee that CENTRIC’s AI-AI can be implemented in practice, we will also explore and develop innovative hardware computing substrates with realistic and AI-AI-compatible energy-efficiency properties. This includes novel electronics such as neuromorphic computing and mixed analog-digital platforms. CENTRIC will make this possible by advancing theory, algorithms, hardware co-design, and training and monitoring environments based on digital twins. We will focus on providing the desired quality of experience (QoE) to a given user, or type of users, while optimizing spectrum usage, minimizing energy consumption and guaranteeing EMF compliance.
The results of CENTRIC will be validated and demonstrated in laboratory prototypes and its breakthroughs will enable future 6G use-cases, such as self-driving vehicles, the internet of nano bio-things, or multi-sensory holographic communications.
THE USER-CENTRIC AI-AIR INTERFACE (AI-AI)
User Objectives
App QoS requirements
Societal KVI requirements
Deployment Scenario
Hardware limitations
User objectives & other requirements
CENTRIC Training Environments
CENTRIC waveform & transceiver learning
CENTRIC protocols learning
CENTRIC computing platform
CENTRIC Training environments
User-centric AI-AI Plateform
Application
User-centric stack
User CENTRIC platform
OUR VISION
CENTRIC positions the AI-AI as the essential fabric of future wireless connectivity systems. Among the beneficiaries of this approach are naturally mobile network operators and the private network’s market, which will profit from highly customizable systems wherein different customers have entirely distinct personalized needs. For instance, a university campus is unlikely to have the same connectivity requirements as an indoor smart factory. As humanity ventures into the future, new and radically different communication needs will emerge. Addressing them with a traditional multi-purpose wireless standard would significantly limit the scope of future applications, and potentially prevent many cutting-edge inventions from fulfilling their potential. CENTRIC aims at being “future-proof,” endowing the networks of tomorrow with the AI tools to support a range of new applications.
In this project, we advocate for an approach to 6G communications whereby the application’s requirements define the starting point for the design of the underlying protocol stack. As the example above illustrates, this is not yet possible today, as vendors of telecom equipment simply cannot produce a new stack for each new application and scenario.
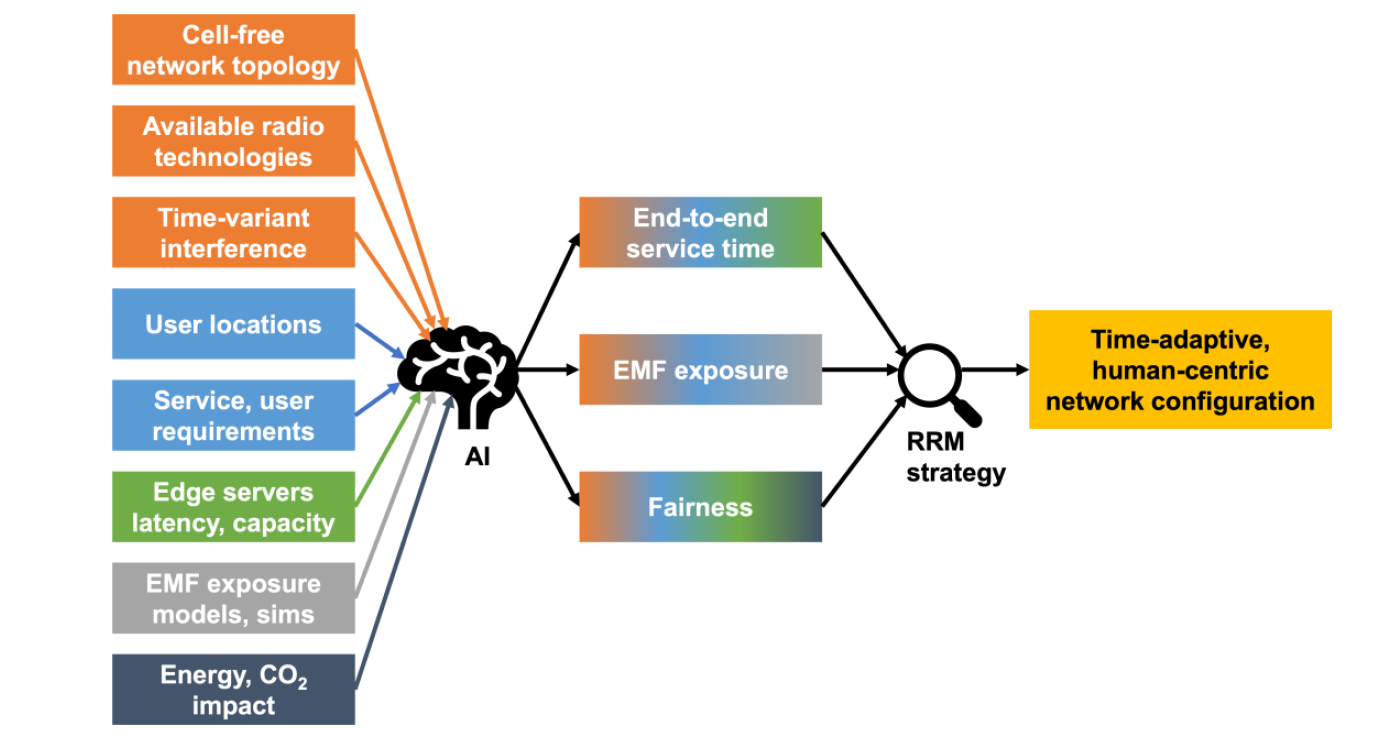
The following everyday example can help illustrate how the CENTRIC project consortium envisions AI-powered user-centric communications in the 2030s. CENTRIC will explore and deliver AI-based breakthroughs in some of the most pressing 6G RRM areas, such as sustainable data management at the wireless edge, EMF exposure control in novel network architectures and energy savings. Today, one can buy a smart lightbulb from Osram, another one from Philips, and a gateway from Ikea and it is still a significant challenge to get them to work together seamlessly. Despite numerous attempts in the past decade (involving common protocols, gateway designs and standards) the fragmentation of the smart home market still prevents these so-called smart devices from communicating with one another to solve the simplest of use-cases: turning on the lights. The incompatibility between these systems occurs at various layers: At the physical layer, some systems use Zigbee, others Bluetooth, and so on. At the security layer, not all systems may use the same encryption mechanisms or key exchange algorithms. The application layer is, however, remarkably similar across all these systems (it switches, regulates colour temperature, brightness, etc.).



